End-to-end encryption (E2EE) is considered as a communication system where only the communicating users can read the messages. Such communicating messages cannot be read by potential eavesdroppers which even include internet providers, communication service providers and telecom-services providers.
End-to-end encryption also prevents easy access to cryptographic keys needed to decrypt the conversation. This communication system defeats all the attempts of radaring, surveillance or tampering of data(messages). This also states that companies which are using end-to-end encryption cannot hand over the text messages of their customers to the authorities.
End-to-end encryption (E2EE) as a method can be used for securing encrypted data while the data moves from the source to the destination. The main aim of E2EE is to encrypt the data at the web level and then to decrypt the same on database or application server level. End to end encryption if implemented with trusted algorithms, ensures the highest level of data protection.
It is always the user who initiates the encryption from a source device in the process of end-to-end encryption. This offers users greater flexibility in deciding which data to encrypt? In encryption process, however, other details such as the addresses, routing information, headers, and trailers are not encrypted.
Let’s look at the advantages of end-to-end encryption:
- Selective encryption offers great help in case of encryption of sensitive data hence user gets greater flexibility in deciding which data to encrypt.
- End-to-end encryption offers the ability to choose specific configurations which help in higher modularization of the functionality.
- The file size involved in the process is quite small and thus the processing uses only minimal (and sufficient) resources and encryption time.
Going forward, let’s understand Advanced Encryption Standard (AES), an important and popular type of End-to-End Encryption.
Advanced Encryption Standard (AES)
AES encryption was originally known as Rijndael. It is a specification for the electronic data encryption. AES encryption is used in various chatting applications where data encryption technique is used. Let us learn about it in the form of these Q&A for a change.
Q1: What is AES encryption?
A1: AES encryption algorithm allows encryption and decryption of text. 128, 192 or 256-bit long key size can be used for encryption and decryption. This results in a downloadable text file. AES (acronym of Advanced Encryption Standard) is a symmetric encryption algorithm which was developed by Belgian cryptographers naming Joan Daemen and Vincent Rijmen. It was designed to be efficient in both hardware and software which supports a block length of 128 bits and key lengths of 128, 192 and 256 bits.
Q2: When is it helpful to use AES encryption?
A2: AES encryption and decryption algorithms are greatly helpful for securing and sending sensitive or confidential data. It fosters encrypting a confidential text into a decryptable format, but decryption of encrypted text is possible only if you know the right password.
Q3: How secure is AES encryption algorithm?
A3: AES encryption is quite a secure process which is used by U.S. for securing sensitive but unclassified data.
Understanding Diffie Hellman Key
Diffie Hellman is an algorithm which is used to establish a shared secret between two parties. Diffie Hellman is a method of exchanging cryptographic keys which is used in symmetric encryption algorithms like AES.
An anonymous key agreement protocol, Elliptic curve Diffie-Hellman (ECDH) allows two parties (each having an elliptic curve public-private key pair) to establish a shared secret process over an insecure channel. The DHE key exchange method, therefore, allows two parties, who have no prior knowledge about each other, to jointly establish a shared secret over an insecure channel. Using symmetric key cipher, this key can be used to encrypt subsequent communications. DHE and ECDHE are foundation stones of conventional SSL secure web connection protocols. DHE is slower but on the contrary, ECDHE supports all major browsers.
The same can be explained in a more simplified way by the image below.
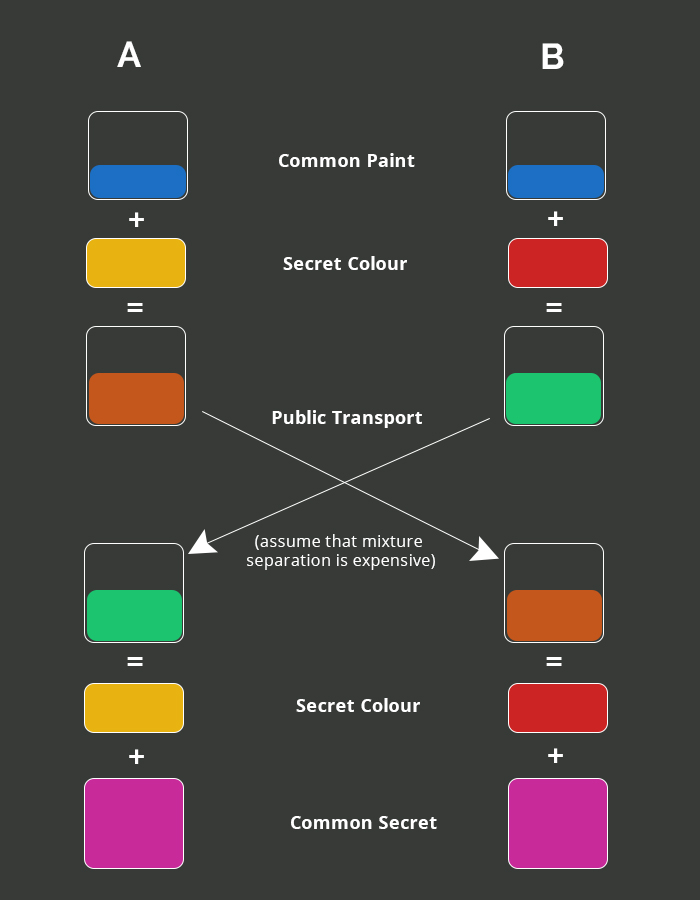
Need For ECDH
AES encryption algorithm also works without ECDH, but the problem is that we will then have a fixed secret key on both ends. Thus we will need to hardcode the key in the .apk file which can again be decompiled or not that if we get it from the server then, in that case, any dictionary attack could work. Hence, to avoid such conditions we have to use ECDH key exchange algorithm which allows us to change keys for even every individual set of conversations if we like.
This can be well-explained with an example like if A chats with B a different key would be generated to encrypt messages known only to these two and it will be very different from the key that is shared among J(a new chat buddy) and A. This is how an end-to-end encryption is achieved – imagine a hundred private tunnels for a hundred different chat threads.
WhatsApp has implemented the same. The world’s largest messaging service has rolled out end-to-end encryption for its billion users across all devices, including Android, iPhones, Blackberry, Nokia, and Windows phones. WhatsApp adds full encryption across its service. It uses “The Signal Protocol”, designed by Open Whisper Systems, for its encryption. With its latest version, every message, photo, video, file, and call made via WhatsApp will be completely secure. This ensures that nobody except sender and receiver will have access to its content – not even the WhatsApp employees.
Need help in achieving end-to-end encryption? Contact us at [email protected].
References: Wikipedia, andrea.corbellini.name, aesencryption.net, nkumar83.wordpress.com, core.telegram.org, codota, github, techopedia, telegraph.co.uk, indianexpress












